Cybersecurity Threat Analysis
The following use case demonstrates how TeraVM is used with Cybersecurity Threat Identification & Analysis
Cybersecurity
The ability to deliver and maintain effective security defences, to protect against malicious exploits, is becoming an exhaustive and cost prohibitive exercise, especially in the light that many new vulnerability types are being exposed on a daily basis.
Challenges:
- Cybercriminals are using more sophisticated attack mechanisms
- Attacks can originate from a personal networked device or from shared server compute resources to expose vulnerabilities.
- Attack types range from vulnerability scans to distributed denial of service
- Increased ferocity, unknown duration and scale of attacks
Cybersecurity Threat Identification
The ability to detect the presence of an exploit traffic threat signature on the network is the first line of protection for many security defences. However, as cybercriminals continuously evolve the attack type, the assurance that the security defence or ruleset is maintained is critical to ensure that the evolving threat signature is blocked effectively.
Obstacles:
- Assessing exposure to vulnerability is time consuming
- Requires regular referencing of the publically maintained Common Vulnerability and Exposure (CVE) lists.
TeraVM Cybersecurity Threat Analysis (TVM – CTA)
Today, security defence providers and consumers of their products need a more agile approach which enables them to efficiently assess security defences, ensuring maximum protection is maintained on an ongoing basis.
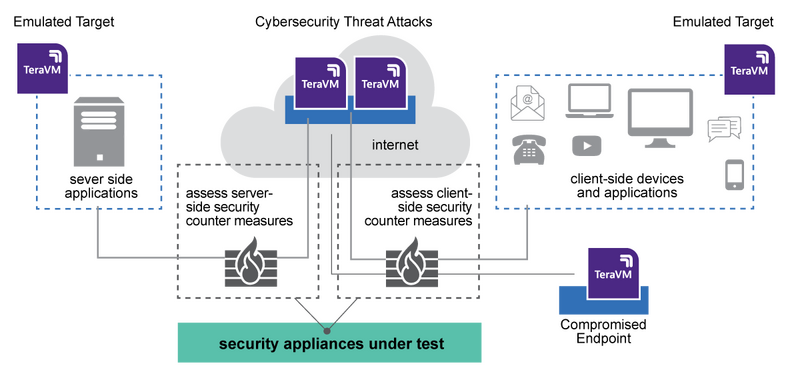
TeraVM is the solution of choice for many as it enables a progressive and agile environment to assess the effectiveness of security counter measures. TeraVM is used to determine the ability of security appliances to stop security threats destined for network attached equipment of: user endpoints, applications, networking infrastructure and server side appliance and applications.
TeraVM’s Cybersecurity Threat Analysis provides:
- Regularly maintained set of traffic threat signatures which references the industry standard Common Vulnerability and Exposures (CVE) repository.
- The necessary agility and automation to continual assess security defences against the thousands of CVE profiles
- Progressive updating of security defences against the latest vulnerabilities, protocol attacks and malware threats by pin-pointing potential vulnerabilities
- A safe and controlled environment to assess security policies