High-Fidelity Threat Forensics and Remediation
Observer delivers comprehensive end-to-end network forensics to eliminate blind spots, minimize dwell time, and accelerate remediation.
High-fidelity describes a century-old commitment to detailed reproduction that accurately represents the details of the original source. With each new data breach costing targeted businesses over $4 million on average, the time has come to apply this enhanced level of rigor to network security. VIAVI threat forensics leverages the power of packet capture and enriched flow records to establish unprecedented real-time and historical threat visibility.
Your network has so much it wants to tell you. Hybrid networks have never been more complex. The proliferation of IoT devices, and 5G adoption has only increased the potential for security vulnerabilities. Firewalls, antivirus software, IDS, and DLP systems provide essential layers of detection and prevention, but what happens when attackers inevitably evade detection and penetrate the security perimeter?
VIAVI Observer acts as a 24/7 security camera, continually monitoring and analyzing data sources from nearly every device and infrastructure entity to assess what’s connected, who’s communicating, and what’s being transacted from end to end.
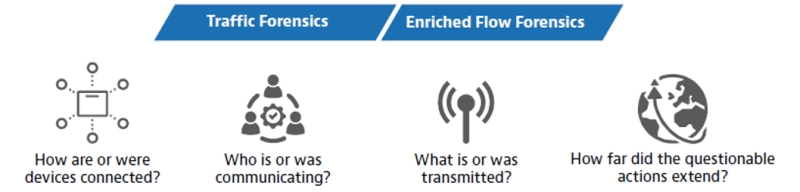
High-Fidelity Threat Forensics Pain Points
Observer’s High-Fidelity Threat Forensics address many of the pain points felt by SecOps and NetOps teams as they strive for improved visibility and faster response times when security incidents occur.
- Visibility Gaps: Network visibility is impeded by organizational silos, repeated IP address translations, and an inability to interpret unstructured data sources. The resulting gaps in real-time and historical visibility require a manual “stare and compare” analysis mode that exposes more sensitive business and customer data as the clock ticks.
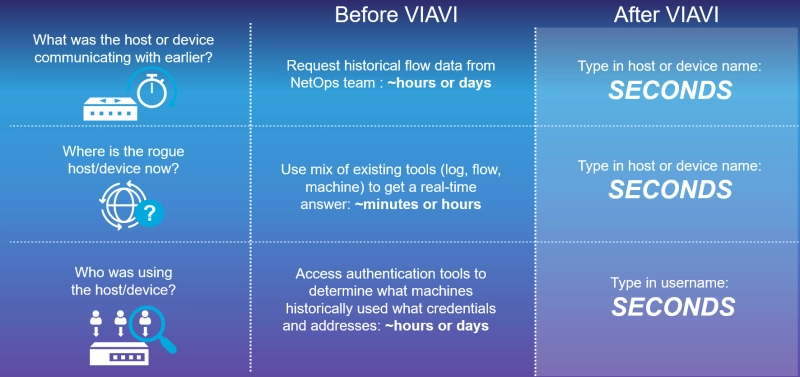
Observer enhances visibility by combining structured data sources with unstructured Syslog, infrastructure, and active directory (AD) data. The resulting enriched flow records clearly illustrate the relationships between User, IP, MAC, and application usage in the network. - Security Team Blind Spots: Security teams armed with tools such as IDS, IPS, firewalls, and VPN concentrators, and are the modern-day gatekeepers protecting the entry point from intruders. When a security breach does occur, they need to understand the full extent of the breach, the location of the rogue host or device, and the impacted assets as soon as possible to remediate and end the threat. Threat forensics fill in the gaps to minimize blind spots for NetOps and SecOps teams, reducing dwell time from hours or days to seconds.
Use Cases
Despite the expanding diversity of industries and applications, all network owners and users share a personal stake in protecting their data, applications, and other valuable assets from theft or compromise.
- Healthcare
Protection of confidential information and compliance with regulatory standards (HIPAA) enacted to safeguard patient privacy are of the utmost importance in the healthcare industry. High-fidelity threat forensics adds value by pinpointing the exact source and extent of a breach quickly to minimize patient record exposure and determine appropriate remediation actions. - Financial Industry
High dollar value assets in the financial sector make these networks prime targets for hacking, insider threats, and fraud. The visibility provided by High-Fidelity Threat Forensics provides the ironclad evidence needed to identify internal or external threats while establishing the data granularity needed to support zero-trust access policies. - Retail Industry
Retailers and eCommerce proprietors regularly handle vast amounts of sensitive customer, POS, and financial data. The improved incident response metrics engendered by enhance customer trust and resilience to future attacks while supporting compliance with industry regulations including GDPR and PCI-DSS. - Manufacturing
While sensitive customer data is less likely to be exposed in a manufacturing environment, these networks must protect essential intellectual property and trade secrets as products are designed, built, and shipped. High-Fidelity Threat Forensics also improves operational resilience by supporting the investigation of system and infrastructure anomalies.
The VIAVI Approach – Unparalleled Forensic Value
Prevention and detection are principal elements of network security, but threat forensics brings an intangible ingredient to the table. When threats inevitably elude front-line defenses, Observer allows you to streamline the remediation process (and minimize dwell time) by quickly determining how the attackers got in, how long they were there, where they went, and what they took. By tracking and recording lateral movements, Observer characterizes the scope and severity of the breach while providing deeper insight into the tactics employed by bad actors.
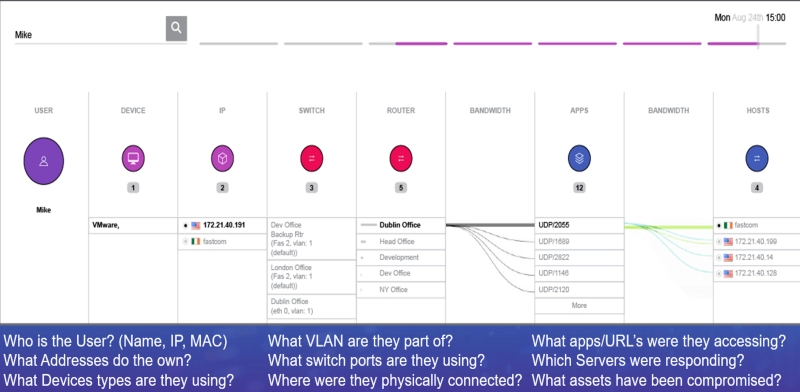
- NAT/PAT: Network and port address translations (NAT/PAT) introduce inline changes to IP addresses and credentials that make it difficult to trace conversations and lateral movements. The rise of remote working and hybrid cloud architecture have added to this dilemma. Observer analyzes NAT/PAT data from all address-translating devices to construct a detailed end-to-end view of each transaction. SecOps teams can leverage these advanced capabilities to identify threat activity while NetOps teams gain a more insight into the end-user experience and problem domain identification.
- Robust Forensics: Reliable forensic evidence is characterized by authenticity, integrity, and probative value that produces an ultimate source of truth. VIAVI high-fidelity threat forensic capabilities meet this high standard by taking full advantage of available data from multiple sources (IPFIX/NetFlow, etc., Active Directory, Syslog, SNMP, packets) and establish a complete forensic footprint that cannot be hidden by bad actors.
The VIAVI Value
With each data breach taking SecOps teams an average of 277 days to contain, threat visibility has become a critical problem to solve. VIAVI offers a robust, compact, and scalable end-to-end high-fidelity forensics solution with advanced features and capabilities unparalleled in the market.
- Forensic Footprints: The ability to store enriched flow records in the form of full-fidelity forensics combined with the packet retention capabilities of Observer GigaStor allows SecOps teams and NetOps teams to retroactively analyze any network transaction and establish unprecedented network visibility.
- Enriched Flow Records: Observer is the only available solution to intelligently combine structured and unstructured data sources to create a “super-record” for every conversation throughout the entire infrastructure and path. Conventional (non-enriched) flow records are often limited to Layer 3 switch and router data.
- Integrated Data Sources: Siloed data can be as ineffective as Siloed IT operations. Observer integrates both its packet and flow data forensics seamlessly into actional able views within Observer APEX.
VIAVI High-Fidelity Threat Forensic Solutions
The VIAVI Observer Platform is the product of decades of collaboration with network administrators, operations teams, and network security experts. Observer takes threat forensic practices to the next level by utilizing pre-defined workflows and high-level dashboards. Components of the modular Observer Platform combine to support business goals while overcoming key network visibility, technology, and asset management challenges.
- Observer GigaStor: The industry-leading packet capture, analysis, and storage solution is now available in two different virtual versions to maintain visibility in all hybrid IT/cloud hosting environments. Full packet capture and metadata-only options provide alternatives based on storage and cost constraints.
- Observer GigaFlow: Enriched flow records integrate network, infrastructure, and user data into a single record carrying in-depth application and traffic information. GigaFlow streamlines network analysis, capacity planning, and cybersecurity investigations by providing all IT stakeholders and business leaders with comprehensive network visibility.
- Observer Apex: The centerpiece of the Observer platform is also the industry’s first performance monitoring solution to generate an End-User Experience (EUE) score for every client/server flow. Flexible dashboards support problem identification and root cause analysis based on all available data sources to reduce mean time to resolution (MTTR).
White Papers & Books
Webinar
Let Us Help
We’re here to help you get ahead.
