5G Security
Together we take 5G security to the next level.
Skip to the following: gNB Security , 5G NSA Security, Open RAN Security,
Secure RAN Intelligence , Core Network Security, Open Secure Cloudification.
Deliver fully secure 5G with intelligent network solutions from VIAVI. Across NSA, SA and O-RAN
Cybercrime will cost companies worldwide an estimated $10.5 trillion annually by 2025, up from $3 trillion in 2015.
New services will exist over 5G networks, as well as the huge variance of new and legacy technologies that will be connected to these networks.
When deploying 5G networks, whether NSA, SA or based on O-RAN specifications, you need to ensure that the network is not just performing at maximum efficiency but is highly secure.
Testing the Security of 5G Base Stations (gNodeBs - gNBs)
The first step of securing a 5G network is adequately testing gNodeB base stations to confirm they are secure and performing the protocols set by 3GPP standards.
When setting up and configuring gNBs, the hardware needs to be validated to ensure that attackers cannot modify settings or software configurations via local or remote access. gNBs also need to be tested to ensure they are resistant to physical attacks. User plane data and control plane data, in particular, are not encrypted in the gNB so must be kept secured.
Security protocols related to the gNB include ciphering user and signalling data as it travels between a user device (UD) and the base station. 5G supports a unique Access and Mobility Management Function (AMF) which operates as the access point to the 5G core, activating the NAS ciphering and integrity protection algorithms that protect user and signalling data. Authentication processes like the Security Anchor Function (SEAF), which is also new to 5G, and handles authentication between a user device and the network, must also be tested to ensure that only vetted devices access the network.
Watch the impact on a 5G network from a DDoS attack:
RAN Threats
Distributed Denial-of-Service (DDoS) is one of the oldest forms of cyberattack, with the first reported attack occurring in 1996. Despite this, DDoS attacks are becoming more sophisticated and more powerful every year - as well as far more diverse in nature and motive. While DDoS has traditionally targeted the availability of services, modern cyberthreats can include DDoS attacks as part of a 'breach kit' aiming to infiltrate a 5G network and target its data.
Downgrade attacks seek to force connections to drop to an older, less secure standard to take advantage of vulnerabilities. In 5G, a downgrade attack can be used to circumvent the 3GPP release 15 (the first 5G standard) that protects 5G devices from IMSI (subscriber ID) theft. Since IMSI catching is still possible in LTE networks, a downgrade attack can deploy a fake base station to steal the user identity of a 5G device.
Man-in-the-middle (MITM) is an older cybercrime technique that has a wide range of uses and aims in the present day. Bad actors intercept the traffic between the victim and the network host to steal information, spy on communications or corrupt data. While MiTM attacks are most commonly performed via wire networks or WI-FI, it is also possible via base stations. Authentication protocols (AKA) are designed to prevent, this but flaws in these agreements are common.
The complexity of 5G network architecture not only increases the surface area for potential attacks but also the chances of network misconfiguration. As the industry begins to adopt 5G core networks and Open RAN, this risk is only increasing. Misconfigurations can not only reduce the performance of the network but also open up security vulnerabilities.
Fuzzing is an automated process that is used to find vulnerabilities in network protocols. It is often used by development teams for testing cycles and involves sending random inputs into the network in an attempt to cause a crash or error. Threat actors can use the same process to find zero-day vulnerabilities.
5G Non-Standalone Security Challenges
In non-standalone (NSA) networks the LTE node (eNB) functions as a master base station, while the 5G (gNB) acts as a serving station. This is known as dual connectivity and enables a 4G and 5G connection to occur at the same time. User data decryption occurs in the gNB as normal but unencrypted (cleartext) data is available in the eNB meaning it must be secured against threats.
Dynamic spectrum sharing enables this parallel use of LTE and 5G frequencies, it breaks packets into slices and delivers them over the same bandwidth. In the event of a cyberattack, operators can partition the affected nodes to limit the attack. This requires close monitoring of the network to identify threats, and as more 5G short-range antennas are added to the network, the increasing entry points increase the level of risk.
Testing the Security of Open RAN Architecture
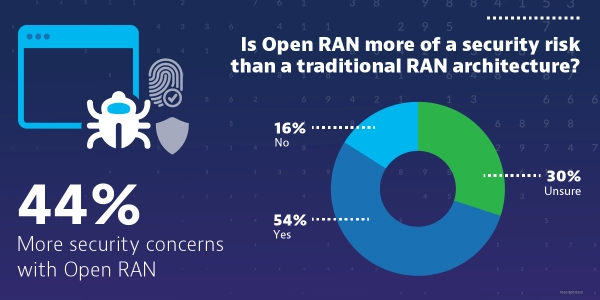
Open RAN is an important evolution in radio networks, preventing vendor lock-in and resulting in a more open, performance-driven ecosystem. However, the setup and integration of these networks is often more complex, so it is vital to perform thorough testing of the network.
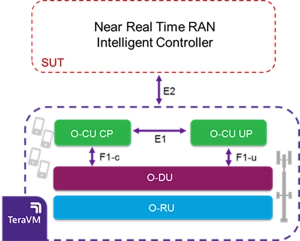
Open RAN uses unique interfaces which apply to the split components of the O-RAN network. The F1 interface applies to split DU-CU implementations while the E1 is for different CU-CP/UP components. Standards for both of these are defined by 3GPP and cover confidentiality, integrity and replay protection, so it is important to audit the network to ensure these interfaces meet 3GPP standards.
Other security considerations for Open RAN are:
Building disaggregated networks requires multi-vendor testing and a comprehensive testing cycle including lab validation, field deployment and network assurance. VIAVI is an expert in this field, and created the industry's first Test Suite for O-RAN Specifications.
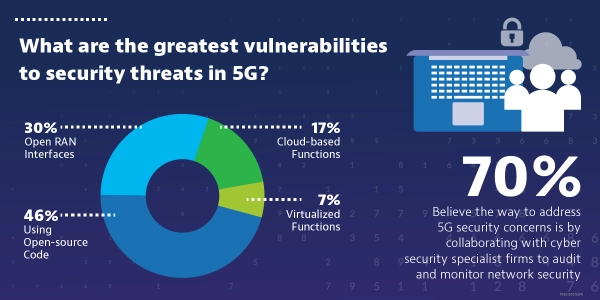
While invaluable for modern development teams, open-source software does present a security risk as vulnerabilities are common. In fact, 65% of telecom professionals believe it is the biggest security risk to 5G networks. Any open-source software used on the network needs to be thoroughly audited to find and fix any potential vulnerabilities.
RIC Security
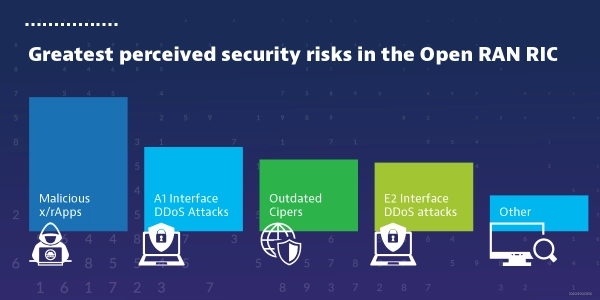
A RAN Intelligent controller (RIC) is a central component of an open and virtualized radio network. It supports the interoperability of different components within an O-RAN and makes intelligent decisions to optimize its performance. Since messages coming into the RIC need to go over the E2 interface, testing the RIC often requires an emulated network. The Viavi TeraVM emulates the RAN and its traffic scenarios to fully stress-test the RIC and identify security vulnerabilities before implementation in a live environment.
xApps and rApps - x/rApps are an essential part of the RIC and ensure smooth network automation in real time. However, as these are developed by third parties, the risk of malicious apps that infect or compromise the network is high. It is important to audit and test these apps before integrating them into the RIC.
Mutual authentication (or Zero-trust) is used in the RIC to safeguard against breaches and malicious components, but this must be tested to confirm authentication processes are correctly blocking malicious traffic.
Securing the Core Network
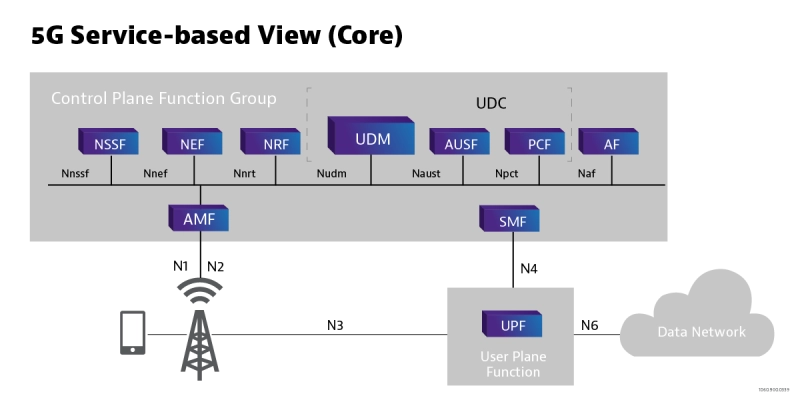
The 5G core utilizes a Service-Based Architecture, where data and functionalities are delivered via a range of connected Network Functions (NF). The 3GPP defines these functions, with each NF having the authorization to access each other via mutual authentication - supporting confidentiality and integrity of the network.
The Network Repository Function (NRF) essentially houses all of the NF functions in the network, this too is secured through mutual authentication. Network Exposure Function (NEF) supports secure access to the exposed services and capabilities of the network, safely allowing third parties to access the network. Naturally, these functions need to be fully secured and tested to ensure that only authorised access is given to the network.
Security Edge Protection Proxy (SEPP) is key to securing the 5G core network. SEPP protects control plane traffic exchanged between different networks. It acts as a security gateway for the home network, performing message filtering, policing and topology hiding. The VIAVI TeraVM 5G Core Test emulates thousands of base stations and millions of UE's to fully stress test the 5G Core. It fully supports 3GPP interfaces so can be used to ensure the security and compliance of 5G Core services.
Next Generation Firewalls
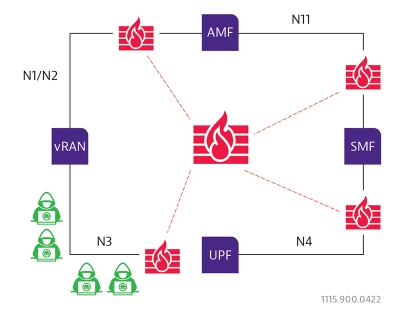
Keeping malicious traffic out of the core network - one of the easiest forms of mitigation is to differentiate between good and harmful traffic. The way to do this is using a firewall.
By inserting firewalls on the N1/N2. N3, N4 and N11 interfaces malicious traffic can be intercepted and removed before getting further in the Core Network.
Read more about this cybersecurity solution for 5G here.
Post-Quantum Cryptography
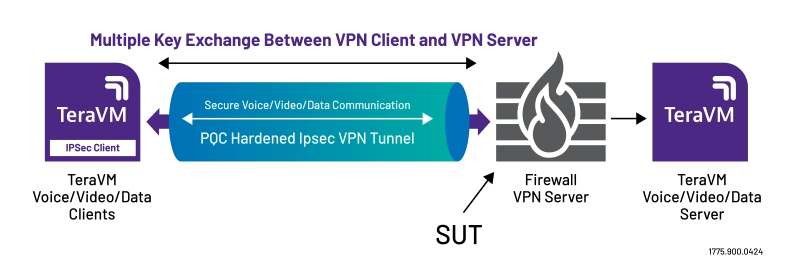
TeraVM has been testing NGFW for over a decade and has introduced Post-Quantum Cryptography testing to allow Post Quantum algorithms as defined in NIST 3 and NIST 4 submissions to be used with TeraVM IKE/IPSec client emulation for:
- Benchmarking the performance of Enterprise devices, Content Delivery Networks, endpoints that initiates or terminates IPSec Traffic using Post-Quantum Cryptography encryption
- Help assess performance impact of key KPI's – Throughput, CPS rate against a new Post Quantum Cryptographic System (PQC) enabled IPSec Gateway
- Testing multiple and large Key Exchanges as outlined in RFC9370 and RFC 9242
The Cloud, Virtualization and Network Slicing
5G networks are far more digitized than previous generations - virtualization, cloud hosting and new services like network slicing make the networks less centralized and more software-led than ever before. This has security implications not seen before in LTE, so testing needs to be a priority to identify potential vulnerabilities.
While the virtualization of edge, 5G core and RAN gives operators more flexibility when building networks, it involves numerous different parties in the development process. This results in more entry points and higher chances of misconfigurations.
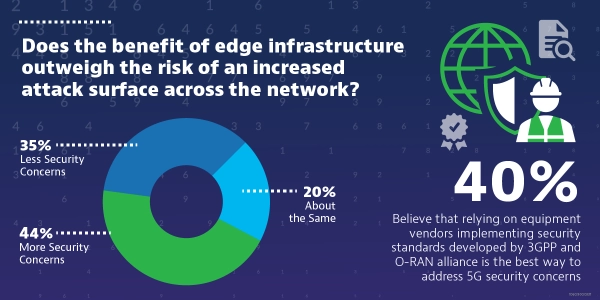
As more and more CSPs choose to host their 5G core networks on the public cloud, having adequate security to account for the increase in entry points is crucial. 5G cloud deployments use a zero-trust architecture (ZTA) built around authentication, monitoring and threat detection and response.
5G has also introduced the ability to network slice, overlaying multiple virtual networks in combination with virtual network functions (VNF) to accurately provision as much capacity as needed for selected services. This functionality is relatively new in the industry and opens up new risks such as cyber criminals targeting a specific network slice or host. As network slicing becomes more common, this must be adequately tested to identify vulnerabilities.
How can we help?
VIAVI has an end-to-end portfolio encompassing robust tests, verification and assurance, and solutions for all aspects of the 5G network.
The VIAVI TeraVM can thoroughly stress test elements of the 5G network by emulating the rest of the network, including thousands of base stations and millions of UE's.
Литература
Постеры
White Papers и книги
Позвольте вам помочь
Мы всегда готовы оказать вам всю необходимую помощь.
