TeraVM is an application and security performance validation solution and is used for functional and performance testing of both the network function and service deployment, covering a range of network and security devices providing comprehensive coverage for assessment of:
- Vulnerability exposure: TeraVMs cybersecurity threat database enables users assess security perimeter performance with the latest cybersecurity threats
- Access/Authentication/Authorization: TeraVM supports the widest range of 3rd party VPN clients, Single Sign On (SAML) and endpoint remote access connection (EAP-MD5)
- Policy management: TeraVM’s per flow emulation of endpoints and applications enables validation of several policy management solutions; including BYOD and blacklisted URL/DNS
Test With Real VPN Clients
TeraVM can be used to act as many individual users on a network, including VPN based users such as Cisco AnyConnect SSL VPN clients with applications, Cisco AnyConnect IPsec VPN clients with applications. This is not ‘simulation’ of VPN traffic, but rather TeraVM acting as real remote workers making many individual valid connections on Cisco FTD/ASA and sending and receiving application flows. TeraVM measures both performance of VPNs and applications in real time. TeraVM also emulates and measures other VPN clients at scale.
Targeted Device Testing - VIAVI is used extensively in testing performance of secure VPN appliance, enterprise call management devices, firewalls, IMS Session Border Controllers and layer 4-7 application scalability. Read more about our VPN Client Emulation use case
Minimize Risk with Threat Analysis
With almost daily reports of security breaches and a large number of firms reporting the detection of an attempted attack on their organisation’s IT systems, never before has it been so critical as to identify where potential security vulnerabilities exist.
Security and attack types take on many guises from bot-attacks to employee credential theft and impersonation on the network.
Many online reports today typically highlight breaches in the form of:
- Viruses, spyware or malware: the outcome of which is theft of money, intellectual property
- Weak or non-existing security access policies: Internally a weak BYOD policy, external poorly implemented authentication service
- Impersonation: via phishing emails or access to fraudulent online websites
- Securing for the unknown, finding vulnerabilities with TeraVM
Knowing where potential vulnerabilities exist is key to enabling greater and more robust security. The challenge for many is the need to validate the reliability of secure access technologies, BYOD device policies and to continually monitor security perimeter performance.
Read more with our Cybersecurity Threat Analysis use case
Post Quantum Cryptography
The implementation of Post-Quantum Cryptography (PQC) protocols introduces additional network performance overhead, impacting end-user experience. Testing is essential for developing and deploying cryptographic systems, including PQC-based ones. Post-Quantum Cryptography aims to create secure algorithms against quantum computer threats. Testing assists in several key areas for Post-Quantum Cryptography:
- Security Assurance
Algorithm Resistance Testing verifies PQC algorithms' resistance against cryptographic attacks. This includes testing the algorithms under different scenarios, including those that utilize classical and quantum algorithms, to evaluate their resilience. - Performance Evaluation
Computational Efficiency: Testing evaluates PQC algorithms' computational efficiency. This includes measuring encryption/decryption speed, key generation speed, and overall system performance. Ensuring the efficiency of PQC algorithms is crucial for widespread adoption in practical applications. - Interoperability Testing
Integration with Existing Systems: Cryptographic systems often require interaction with established infrastructure and protocols. Testing is essential to guarantee the seamless integration of PQC algorithms into diverse systems, avoiding compatibility issues. - Standardization Compliance
Adherence to Standards: testing confirms PQC algorithms' compliance with established cryptographic standards, promoting interoperability and consistent implementation across platforms.
SASE Testing
Secure Access Service Edge (SASE) is a new way for employees accessing corporate functions and data securely and efficiently from any location.
The advent of cloud deployed applications and data combined with the diverse working locations has accelerated this change.
IT organizations are faced with the conundrum of providing employees with fast secure access while ensuring the corporate data and security are not breached and the same time ensuring productivity is not hampered by poor latency, throughput and response times.
While SASE is the solution there are many deployment challenges facing corporations:
- What is the capacity of the VPN links between SASE and private applications?
- How much authenticated and unauthenticated web application traffic can my SASE solution handle?
- Does the end user performance vary under different load conditions?
- How many connections can be sustained?
- How much traffic can be carried inside the tunnels?
- Will redundancy work when relied upon?
- Will everything work seamlessly across a distributed multi-Cloud platform?
- Will latency-sensitive applications such as Teams collaboration, VoIP, media streaming, and video conferencing work on demand without service affecting issues?
- Will a cyber-attack compromise performance while data is scrubbed?
The quickest and safest way to a secure roll out of SASE is to vigorously test in the lab.
With TeraVM SASE test you can be sure enterprise employees will receive a secure connection, operational efficiency and 24/7 access anywhere their laptop takes them.
Features
TeraVM enables customers to:
- Build an elastic test bed which scales both vertically as well as horizontally
- Scale vertically from 1 Gigabit per second up to 1 Terabit per second
- Scale horizontally across test locations e.g. same building or geo-location
- Centrally manage and allocate test resources via a license server
- Gain higher utilization rates of a single test bed through license sharing
TeraVM is 100% virtual
- Same test tool used to test physical solutions and/or virtual solutions
- Supports all major hypervisors - ESXi, KVM
- Supports all major cloud platforms - OpenStack, AWS, MS-Azure, Google Cloud, Oracle OCI, Containerization
- Supports 1 GbE, 10 GbE, 40 and 100 GbE NICs Automation and Orchestration
- REST, CLI, Perl, TCL, XML, Java API, Python, Jython
- Cisco LaasNG, Cisco pyATS, Qualisystems (CloudShell) L2-7 Stateful Traffic Application Emulation
- Voice: CUCM, CUBE, VoIP, WebEx, VoLTE, SIP & RTP, MOS
- Video: CMTS, CDN, Multicast, AMT, ABR, IPTV, VoD, OTT streaming, Video conferencing, WebEx, TelePresence, HTTP Video
- Data: TCP/UDP, Teraflow, Ookla speed test, HTTP/HTTPS, SMTP/POP3, FTP, P2P, DNS, Quick UDP Internet Connections (QUIC) Secure Access Firewall/VPN (ASA Firewall, FirePOWER)
- Secure TCP/UDP Protocols (SSL, TLS, DTLS, IPSec IKE)
- Client and Clientless VPNs (Cisco AnyConnect SSL and IPsec)
- 802.1x EAP-MD5, EAP & PEAP with MS CHAPv2 Authentication
- Mobile Secure Gateway validation (S1-U over IPSec) Cybersecurity Threat and Malware Penetration
- 40,000+ attacks (Spam, Viruses, DDoS, Malware), updated monthly
- DDoS attack applications:
- Flood: SYN, Reflective SYN, Reset, UDP, Ping, ARP
- Attacks: Teardrop; UDP Fragmentation; Configurable Rates, Start and Stop
- Spoof Mac addressing
- Mixed application flows: Good, the Bad and your Own
Wireless RAN and Core Emulation
- vRAN: 5G-NR, 4G-LTE, 3G, 2G - 1,000s of RANs
- vCORE: 5G (NSA & SA), 4G-LTE 3G, 2G, Mobility, SecGW, MEC Network Slicing – Millions of UEs and Bearers
- CIoT: IPDD over NAS, NIDD over SCEF at Scale
- WiFi ePDG offload (EoGRE)
Wireless Core Interface Testing
- Support testing across multiple key Core interfaces
- Error Injection over 5G-N2 (AMF)
- Error Injection over 4G-S1 (MME)
-
Segurança cibernética e resiliência
O TeraVM apresenta uma aplicação escalável e emulação de ameaças do mundo real que aproveita ameaças verdadeiras da internet de repositórios comuns de vulnerabilidade e exposição (CVE). Com atualizações frequentes disponíveis, os usuários avaliam sua postura de segurança no cenário de mudanças contínuas para aplicações, ataques e padrões. Saiba mais
-
Acesso seguro e integridade da aplicação
O TeraVM suporta VPNs orientadas sem clientes (SSL/TLS/DTLS) e com cliente (IPsec IKEv1/ v2), com a capacidade de validar o desempenho usando uma série de algoritmos de autenticação, integridade e criptografia. Além disso, o TeraVM permite a validação de desempenho no tráfego de aplicações do usuário que passa pelos túneis seguros, permitindo uma abordagem pragmática para as configurações da política.
-
Migre para NFV com confiança
Com a solução de teste NFV do TeraVM, você garante desempenho, confiabilidade e previsibilidade das suas funções de rede virtualizada. O TeraVM é a única solução de teste disponível que pode ser orquestrada em um sistema NFV como um VNF regular, permitindo que o tráfego como serviço garanta a entrega confiável da próxima geração de serviços de rede. Saiba mais
-
Novas ediçõesInglês
MWC Barcelona 2025: VIAVI Showcases Solutions to Optimize and Secure Networks Over the Air, Through the Cloud and Into Space
-
Novas ediçõesInglês
VIAVI Introduces Performance Testing for Post-Quantum Cryptography Deployments
-
Novas ediçõesInglês
VIAVI Provides Benchmarking and Validation Across Eight Countries at Fall 2023 O-RAN PlugFest
-
Novas ediçõesInglês
VIAVI Introduces NTN and HAPs Network Testing For 5G and 6G Satellite Communication
Literatura
Notas de aplicação
Folhetos
- Accelerate Advanced 5G and 6G Research and Development Projects
- Containerized TeraVM Security Test Solution
- NITRO Wireless Post Quantum Cryptography (PQC) Test
- SASE Test
- TeraVM Ethernet over GRE (EoGRE) Validation for WiFi-offload
- TeraVM Integration with QualiSystems CloudShell
- TeraVM Voice, Video and MPEG Transport Stream Quality Metrics
- TeraVM: Cybersecurity Database
- TeraVM: IMS Messaging
- TeraVM: Security Assertion Markup Language (SAML)
- TeraVM: Teraflow
- TeraVM: Testing LTE/4G Evolved Packet Cores
- TeraVM: Testing Multicast Based Video Services with TeraVM
- Testing Telepresence with TeraVM
Estudos de caso
Data sheets
- AWS Platform Support for TeraVM Data Sheet
- Google Platform Support for TeraVM
- Microsoft Azure Platform Support for TeraVM
- NetSecOPEN on TeraVM
- TeraVM 5G Core AMF Wraparound Test
- TeraVM 5G Core Security Test
- TeraVM 5G SA Core Test for TVM-vRAN SMF Wraparound Test
- TeraVM 5G SA Core Test for TVM-vRAN UPF Wraparound Test
- TeraVM at Cisco
- TeraVM Overview: What is TeraVM?
- TeraVM Specifications
- TeraVM: Oracle Cloud Platform Support
Manuais e guias do usuário
Pôsteres
Versões de software e firmware
Artigos técnicos e livros
- Can we conquer the challenges of open RAN rollout?
- Dimensioning Enterprise Cloud Platforms for Bring Your Own Devices (BYOD)
- FV Enabling Automation and Performance Validation for Network Services and Labs
- NFV Enabling Automation and Performance Validation for Network Services and Labs
- NITRO Wireless Open RAN Test Suite 2024
- O-RAN: An Open Ecosystem to Power 5G Applications
- Performance Testing for Multicast Services Using TeraVM
- SASE Test Explained
- TeraVM Accreditation report for NetSecOpen Test Methodology
- Voice Analysis for Mobile Networks
- VPN Performance Validation
Video
- 5G Core Security Test
- Cisco AnyConnect VPN Testing
- Nexus 1000V Testing with TeraVM
- NFV Service Validation and OpenStack Solution
- Open RAN End to End Automated Testing Demo
- RIC Energy Saving
- Security Access Service Edge (SASE) Test
- Talking O-RAN with Sameh Yamany, CTO
- TeraVM - Testing without Limits
- TeraVM 5G Core: AMF Wraparound Test
- TeraVM Emulates 20,000 VPN Client
- TeraVM F1 Load Generator and O-DU Simulator
- TeraVM O-CU Tester and O-DU Simulator
- TeraVM SA 200 Gbps Throughput
- TeraVM: Cybersecurity Database UI
- TeraVM: Dynamic Goal Seeking Controller
- TeraVM: Enabling validation for NFV Labs with Open Source MANO
- TeraVM: Northbound API testing in OpenStack
- TeraVM: Simplifying Performance Validation for Security
- TeraVM: SMF Bracket Test for 5G
- TeraVM: UPF Wraparound Test for 5G
- Testing 5G NTN in the Lab
- VIAVI 5G Solutions Overview
- VIAVI Dell MWC 2023
- VPN Management Solution
- World's First TeraVM O-RAN O-CU Test Running on AWS Outposts
- x-App Training Traffic Steering Demo
Webconferência
- Cisco AnyConnect VPN Testing
- How do you test 5G Non-Terrestrial Networks prior to space launch?
- Network Slicing – Test Now, Succeed Later
- Nexus 1000V Testing with TeraVM
- NFV Service Validation and OpenStack Solution
- O-RAN Testing
- RAN Intelligent Controller, the heart of O-RAN
- Security Test Considerations for 5G PART 1
- Security Test Considerations for 5G PART 2
- The Sudden Rise of Open RAN
- Understanding 5G: Lessons from the Field
- Open RAN Lab Webinar Series
-
Repair and Calibration
Our products live in rugged environments for over 10 years with 1000s of test connect/disconnect cycles. We will be there to support you to ensure components that require maintenance like connectors, batteries, and software updates to ensure you are ready to test accurately for years to come. We apply factory procedures that use fast, automated calibration and functional verification, maintenance using OEM parts and the application of all engineering change orders and software updates. Services are available through contract Care plans, FleetCare or per incident as requests.
Top 4 Reasons to Choose VIAVI for Your Repair and Calibration Needs:
- Minimize business disruption
- Budget
- Measurement Accuracy and Product Reliability
- Measurement Compliance, TL9000 certification and OEM Standards
-
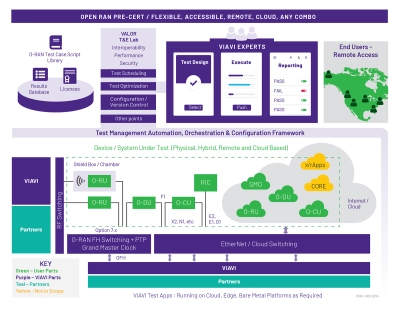
VIAVI Automated Lab-as-a-Service for Open RAN (VALOR)
VIAVI Automated Lab-as-a-Service for Open RAN (VALOR) is a hybrid Lab-as-a-Service and Test-as-a-Service lab based on VIAVI’s industry leading NITRO® Wireless test portfolio. This solution is designed to manage and support 5G and Open RAN projects that would benefit from access to tools and expert staff with a minimal ramp-up time.
Assistência em cada passo
Oferecemos assistência, serviços, treinamento completo e os recursos de que você precisar. Isso tudo faz parte do que fazemos para maximizar o valor de seu investimento VIAVI.
Queremos ajudar
Estamos aqui para ajudar no seu futuro.